For IPSec related theory please go here.
There are 6 steps in the configuration process per router.
1. Configure ISAKMP policy with (HAGLE)
2. Configure Keys
3. Configure Transform Set for IPSec
4. Configure ACL for Interesting Traffic
5. Configure Crypto Map
6. Apply Crypto Map on interface
STEP 01 : Configure ISAKMP policy
This is the step which we define the IKE Phase 1 tunnel parameters which you can remember as HAGLE.
H - Hash Type
A - Authentication Method
G - Groups (DH)
L - Lifetime
E - Encryption Method
R1(config)#crypto isakmp policy 1
R1(config-isakmp)#hash sha
R1(config-isakmp)#authentication pre-share
R1(config-isakmp)#group 2
R1(config-isakmp)#lifetime 60
R1(config-isakmp)#encryption aes
STEP 02 : Configure Keys
R1(config)#crypto isakmp key PASSWORD address 192.168.23.3
STEP 03 : Configure Transform Set for IPSec
Transfrom set is an acceptable combination of security protocols and algorithms.
esp-ace is used for ESP Encryption and esp-sha-hmac is used for ESP Authentication.
R1(config)#crypto ipsec transform-set TRANSFORMSET esp-aes esp-sha-hmac
STEP 04 : Configure ACL for Interesting Traffic
R1(config)#ip access-list extended 100
R1(config-ext-nacl)#permit ip host 1.1.1.1 host 3.3.3.3
STEP 05 : Configure Crypto Map
Crypto Map is where we match the interesting traffic and set the peer and transform set.
R1(config-crypto-map)#crypto map CRYPTOMAP 10 ipsec-isakmp
R1(config-crypto-map)#match address 100
R1(config-crypto-map)#set transform-set TRANSFORMSET
R1(config-crypto-map)#set peer 192.168.23.3
STEP 06 : Apply Crypto Map on interface
R1(config)#int e0/0
R1(config-if)#crypto map CRYPTOMAP
Additionally we will need some routing for IPSec to work too.
R1(config)#ip route 192.168.23.0 255.255.255.0 192.168.12.2
R1(config)#ip route 3.3.3.3 255.255.255.255 192.168.23.3
Same should be configured on R3 as per it's perspective like the following..
R3(config)#crypto isakmp policy 1
R3(config-isakmp)#hash sha
R3(config-isakmp)#authentication pre-share
R3(config-isakmp)#group 2
R3(config-isakmp)#lifetime 60
R3(config-isakmp)#encryption aes
R3(config)#crypto isakmp key PASSWORD address 192.168.12.1
R3(config)#crypto ipsec transform-set TRANSFORMSET esp-aes esp-sha-hmac
R3(config)#ip access-list extended 100
R3(config-ext-nacl)#permit ip host 3.3.3.3 host 1.1.1.1
R3(config)#crypto map CRYPTOMAP 10 ipsec-isakmp
R3(config-crypto-map)#match address 100
R3(config-crypto-map)#set peer 192.168.12.1
R3(config-crypto-map)#set transform-set TRANSFORMSET
R3(config-crypto-map)#int e0/0
R3(config-if)#crypto map CRYPTOMAP
R3(config)#ip route 192.168.12.0 255.255.255.0 192.168.23.2
R3(config)#ip route 1.1.1.1 255.255.255.255 192.168.12.1
Now pings from R1's loopback to R3's loopback and vice versa will work.
For verification,following commands can be used.
show crypto map interface e0/0
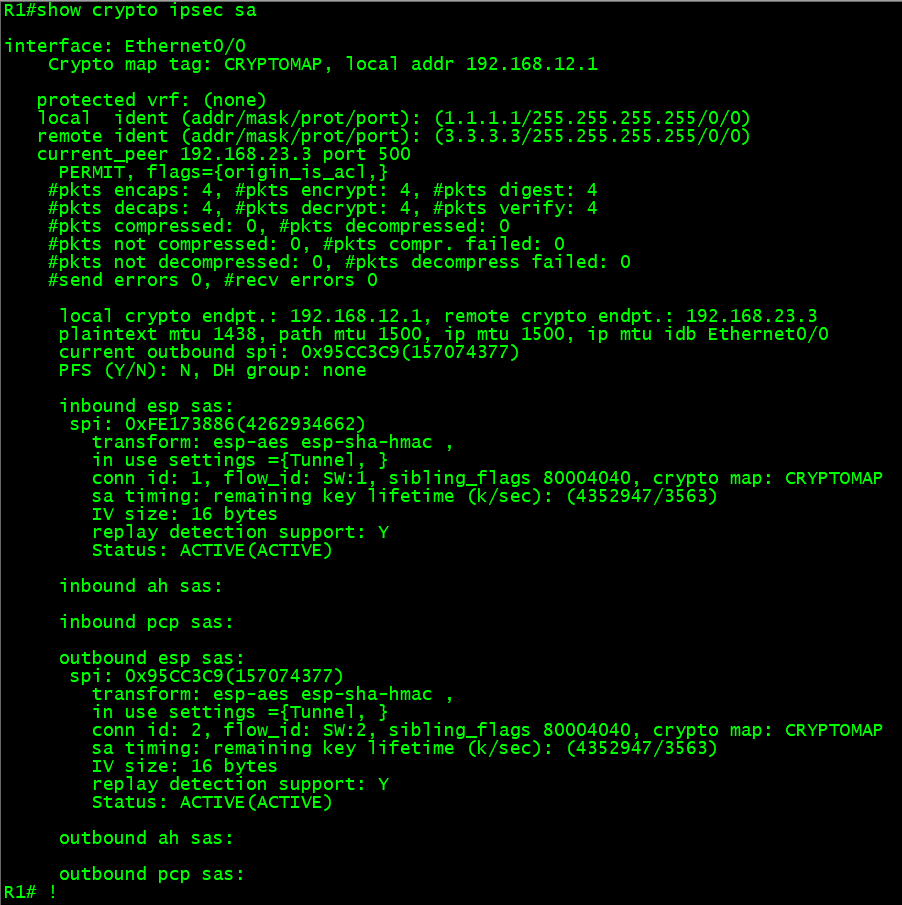
show crypto ipsec sa
Note :-
You may notice that ISAKMP policy is not called per Crypto Map. It will be called for all the VPNs while IKE Phase 1 tunnel is forming. If a separate ISAKMP policy is needed per VPN, ISAKMP Profiles must be configured and must be called in IPSec Profiles per VPN.
Also note that there are 2 SPI (Security Parameter Index) is for each VPN, (inbound and outbound).
Inbound SPI of R1 is equal to the outbound SPI of R3 by value and Outbound SPI of R1 is equal to the inbound SPI of R3.
If you want to see a packet capture for this, please go here.
Also note that in IPSec, an ACL can capture locally generated traffic.
1. Configure ISAKMP policy with (HAGLE)
2. Configure Keys
3. Configure Transform Set for IPSec
4. Configure ACL for Interesting Traffic
5. Configure Crypto Map
6. Apply Crypto Map on interface
STEP 01 : Configure ISAKMP policy
This is the step which we define the IKE Phase 1 tunnel parameters which you can remember as HAGLE.
H - Hash Type
A - Authentication Method
G - Groups (DH)
L - Lifetime
E - Encryption Method
R1(config)#crypto isakmp policy 1
R1(config-isakmp)#hash sha
R1(config-isakmp)#authentication pre-share
R1(config-isakmp)#group 2
R1(config-isakmp)#lifetime 60
R1(config-isakmp)#encryption aes
STEP 02 : Configure Keys
R1(config)#crypto isakmp key PASSWORD address 192.168.23.3
STEP 03 : Configure Transform Set for IPSec
Transfrom set is an acceptable combination of security protocols and algorithms.
esp-ace is used for ESP Encryption and esp-sha-hmac is used for ESP Authentication.
R1(config)#crypto ipsec transform-set TRANSFORMSET esp-aes esp-sha-hmac
STEP 04 : Configure ACL for Interesting Traffic
R1(config)#ip access-list extended 100
R1(config-ext-nacl)#permit ip host 1.1.1.1 host 3.3.3.3
STEP 05 : Configure Crypto Map
Crypto Map is where we match the interesting traffic and set the peer and transform set.
R1(config-crypto-map)#crypto map CRYPTOMAP 10 ipsec-isakmp
R1(config-crypto-map)#match address 100
R1(config-crypto-map)#set transform-set TRANSFORMSET
R1(config-crypto-map)#set peer 192.168.23.3
STEP 06 : Apply Crypto Map on interface
R1(config)#int e0/0
R1(config-if)#crypto map CRYPTOMAP
Additionally we will need some routing for IPSec to work too.
R1(config)#ip route 192.168.23.0 255.255.255.0 192.168.12.2
R1(config)#ip route 3.3.3.3 255.255.255.255 192.168.23.3
1st route is to identify the tunnel destination which should be known via underlay routing and the 2nd route is to identify the destination of the interesting traffic which points to the tunnel destination.
Same should be configured on R3 as per it's perspective like the following..
R3(config)#crypto isakmp policy 1
R3(config-isakmp)#hash sha
R3(config-isakmp)#authentication pre-share
R3(config-isakmp)#group 2
R3(config-isakmp)#lifetime 60
R3(config-isakmp)#encryption aes
R3(config)#crypto isakmp key PASSWORD address 192.168.12.1
R3(config)#crypto ipsec transform-set TRANSFORMSET esp-aes esp-sha-hmac
R3(config)#ip access-list extended 100
R3(config-ext-nacl)#permit ip host 3.3.3.3 host 1.1.1.1
R3(config)#crypto map CRYPTOMAP 10 ipsec-isakmp
R3(config-crypto-map)#match address 100
R3(config-crypto-map)#set peer 192.168.12.1
R3(config-crypto-map)#set transform-set TRANSFORMSET
R3(config-crypto-map)#int e0/0
R3(config-if)#crypto map CRYPTOMAP
R3(config)#ip route 192.168.12.0 255.255.255.0 192.168.23.2
R3(config)#ip route 1.1.1.1 255.255.255.255 192.168.12.1
Now pings from R1's loopback to R3's loopback and vice versa will work.
For verification,following commands can be used.
show crypto map interface e0/0
show crypto ipsec sa

Note :-
You may notice that ISAKMP policy is not called per Crypto Map. It will be called for all the VPNs while IKE Phase 1 tunnel is forming. If a separate ISAKMP policy is needed per VPN, ISAKMP Profiles must be configured and must be called in IPSec Profiles per VPN.
Also note that there are 2 SPI (Security Parameter Index) is for each VPN, (inbound and outbound).
Inbound SPI of R1 is equal to the outbound SPI of R3 by value and Outbound SPI of R1 is equal to the inbound SPI of R3.
If you want to see a packet capture for this, please go here.
Also note that in IPSec, an ACL can capture locally generated traffic.




No comments:
Post a Comment